Splitting
There are different methodologies in regards of splitting entries. Some of our competitors create a single entry even for full patchdays (affecting multiple products), others are dividing as soon as there are multiple arguments affected (to create as many entries as possible to boost their stats). We chose something in between.
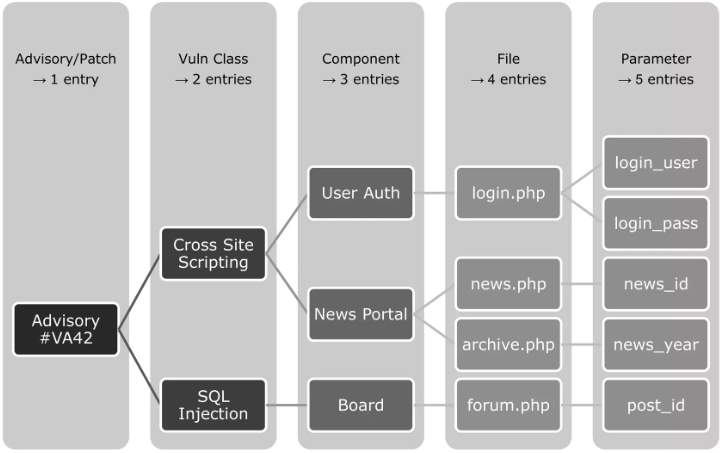
We have multiple factors which affect the decision to split an entry or not. For example our binary analysis has shown that Microsoft Internet Explorer and Microsoft Edge entries shall be divided as they have severe differences. Therefore, even if Microsoft publishes a single advisory/CVE, we have two separate entries.
This would basically duplicate the base data of an entry. Typically the vulnerability class, access vector and advisory details. But there are other fields which might have important differences like CVSS (e.g. Windows versions have often different CVSS according to Microsoft), exploit prices (product dependency), patch details (e.g. IDs and links), vulnerability scanner plugins (different platforms), all threat intelligence data, etc.
The field source_seealso might inform you about entries which are connected with an entry.